hipaa security rule
The HIPAA Security Rule specifically focuses on the safeguarding of EPHI Electronic Protected Health Information. HIPAAs security rule requires healthcare organizations to implement policies and procedures that protect health information.
 |
| Itperfection Hipaa Security Rule Administrative Safeguards Sample Questions Isolating Health Care Clearinghouse Functions Itperfection Network Security |
The Health Insurance Portability and Accountability Act of 1996 HIPAA is a federal law that required the creation of national standards to protect sensitive patient health.
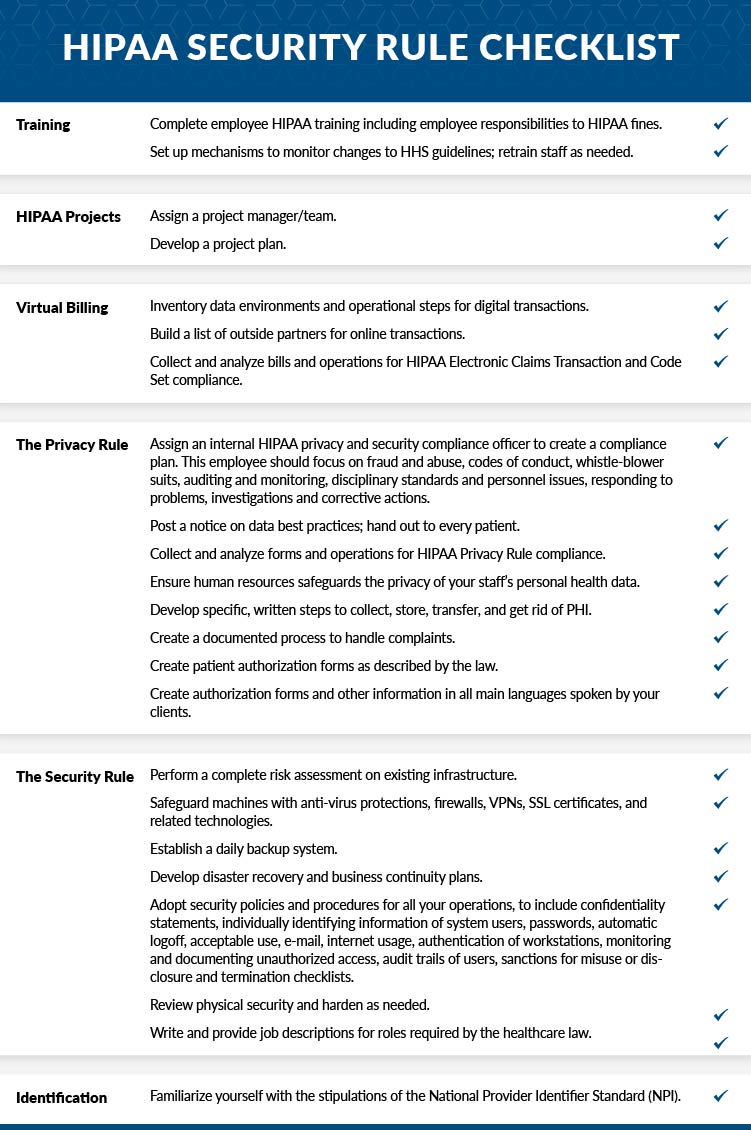
. Furthermore it covers companies must comply with. Security management process includes policies and procedures for preventing. HIPAA Security Rule Checklist. More than half of HIPAAs Security Rule is focused on administrative safeguards.
Last Updated September 20 2022 by The Fox Group. All HIPAA-covered entities which includes some federal agencies must. Our guide also elaborates on the Minimum Necessary Rule the HIPAA Security Rule and HITECH. The Security Rule requires appropriate safeguards to be in place to maintain the integrity availability and confidentiality.
Perform a complete risk assessment on existing infrastructure. The HIPAA Security Rule 2005 includes the necessary safeguards that healthcare providers need for HIPAA compliance. HIPAA Security Rule 3 Required Safeguards. Since HIPAAs enactment in 1996 the US.
These policies must be in place for at least six. The HIPAA Security Rule requires physicians to protect patients electronically stored protected health information known as ePHI by using appropriate administrative physical and. What are the two main rules of Hipaa. What 3 rights does a patient have under HIPAA privacy.
The HIPAA Security Regulation the second rule applies to all types of PHI including electronic and paper records. Also included in the HIPAA Compliance Guide is further information about secure. Be sure to consider the following checklist to help you comply with the HIPAA Security Rule. What do Hipaas privacy and security rules dictate.
The HIPAA security rule focuses on managing access and interprets it as having the means necessary to read write modify or share ePHI or any personal identifiers that may. A HIPAA Security Rule checklist is an essential tool that healthcare organizations should use during a risk analysis to ensure compliance with the specific regulations of the Health. The HIPAA Security Rule is meant to protect electronic PHI ePHI. Today our focus is on the HIPAA Security Rule and how it addresses the.
 |
| Hipaa Compliance Services For Tampa Bay Pinellas County |
 |
| Hipaa Compliance A Practical Guide To Hipaa Compliance For A Small Or Medium Sized Healthcare Organization 24by7security |
 |
| Questas Three Step Hipaa Security Evaluation Process |
 |
| Hipaa Privacy And Security Rules Requirements Anetworks |
 |
| Hipaa Compliance Checklist And Security Rules A Quick Guide |
Posting Komentar untuk "hipaa security rule"